Everytime I deal with SAML it reminds me of the current state of electric vehicles. Like petrol cars all EV’s run on the same type of ‘fuel’, yet unlike petrol cars, there are a number of different plugs and charging methods. SAML as a standard feels just like this.
The Problem
Last week I had to implement an AppStream proof of concept for a client wanting to retire their citrix farm, pretty standard stuff.
They used Onelogin internally for federation and I assumed being a SAML Idp it would be trivial to integrate with AppStream like I have with other providers such as Gsuite and Okta in the past.
AWS provides some documentation required to configure the SAML provider here and covers a number of providers here. So I referenced the majority of the articles to configure an application inside Onelogin, however I constantly saw this error message:
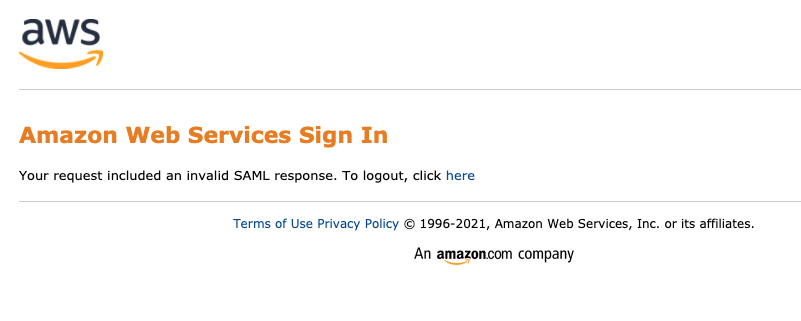
Which is referenced in this AWS troublshooting page stating that the SAML response didn’t include the proper IAM role attributes.
After inspecting the SAML assertion in chrome I could see that the role was indeed being sent, so this left me in tough place. I decided to have a hunt on google for other people that had implemented Onelogin with AppStream but I couldn’t find a single post about it.
The Solution
Luckily working for an AWS consulting partner has introduced me to a number of great people at AWS. I reached out to Richard, part of the End User Computing team (Workspaces & AppStream) to see if anyone at AWS had encountered the same issue but his response was the same as Google’s.
After about a week of trying a number of different settings & raising a ticket with Onelogin we were able to successfully login to AppStream via Onelogin SAML. I’ve been told that in the near future Onelogin will be adding an AppStream application to the catalog with preset settings, however in the meantime, below I have included all the settings you need to be aware of to get Onelogin & AppStream working smoothly.
Create a SAML Test Connector (Advanced) application
Under Configuration:
| Setting | Value |
|---|---|
| Relay State | https://relay-state-region-endpoint?stack=stackname&accountId=aws-account-id-without-hyphens |
| Audience (EntityID) | urn:amazon:webservices |
| Recipient | https://signin.aws.amazon.com/saml |
| ACS (Consumer) URL Validator | ^https://signin.aws.amazon.com/saml$ |
| ACS (Consumer) URL | https://signin.aws.amazon.com/saml |
| Single Logout URL | |
| Login URL | |
| SAML not valid before | 3 |
| SAML not valid on or after | 3 |
| SAML initiator | OneLogin |
| SAML nameID format | Persistent |
| SAML issuer type | Specific |
| SAML signature element | Both |
| Encrypt Assertion | |
| SAML encryption method | TRIPLEDES-CBC |
| Send NameID Format in SLO Request | |
| Generate AttributeValue tag for empty values | |
| SAML sessionNotOnOrAfter | |
| Sign SLO Request | Ticked |
| Sign SLO Response | Ticked |
Under Parameters:
| Setting | Value |
|---|---|
| NameID value | |
| https://aws.amazon.com/SAML/Attributes/Role | RoleARN,IDPRoviderARN |
| https://aws.amazon.com/SAML/Attributes/RoleSessionName | |
| https://aws.amazon.com/SAML/Attributes/SessionDuration | 43200 |
Under SSO:
| Setting | Value |
|---|---|
| Change SAML Signature Algorithm | SHA-256 |
